With the increasing cyber-attacks every year, many are now considering blockchain security for the full protection. Well, blockchain technology is blooming for a long time now, and it is popular for many sectors already.
Starting from supply chain management, healthcare, finance, energy, IoT, and many more now it’s starting to spread into the realm of security as well.
However, many of you are quite skeptical about the whole concept of enterprise blockchain security and whether it’s capable of handling the load.
To help you figure out whether or not you should consider blockchain security for your organization, we are compiling all the necessary information about cybersecurity. So, today, I’ll be talking about everything there is to know about blockchain cybersecurity.
Want to become A Blockchain Security Expert? Enroll in our Certified Blockchain Security Expert (CBSE) Course!
Table of Contents
Chapter-1: What Is Cybersecurity?
Chapter-2: Different Kinds of Cyber Security Threats
Chapter-3: Can Blockchain Fix Cybersecurity?
Chapter-4: Blockchain Security: Possible Use Cases
Chapter-5: Examples of Blockchain Cybersecurity at Work
Chapter-1: What Is Cybersecurity?
Cybersecurity is a way of defending computers, mobile devices, servers, data, networks, and electronic systems from malicious attacks. Some of you may know it as electronic information security or I formation technology security.
You can apply this term in many categories, such as business to mobile device computing. However, mainly, they are divided into six types of category. And in every case security is essential.
- Network Security:
It’s mainly the practice of securing any kind of computer or server networks from intruders. Furthermore, they could be opportunistic malware or any kind of targeted attackers.
- Information Security:
This kind of cybersecurity will protect privacy or data or the integrity of any kind of information in storage or anything that’s being transmitted.
- Application Security:
These are mainly the security protocols that keep the devices or any program free of malware. In reality, a compromised device or application can offer access to the information that it was meant to protect.
Furthermore, a successful security process will begin in the application phase before the application can even affect the devices.
- Operational Security:
Mainly this type of security handles all the decision or processes needed for protecting all the data assets. Furthermore, it’s an umbrella term because a lot of processes falls under the category. In reality, the permission levels or user access restriction rules fall under here.
Furthermore, determining where and how the information would be stored is also a big part of this matter.
- Business Security:
It’s one of the major security procedures. In reality, business security would require a combination of all the cyber-security categories. However, they may require on a large scale. Also, a business has to maintain the firewall service when they have minimal assets or resources. Thus, many security protocols are designed to use less resource but offer more outputs.
- Disaster Recovery:
It’s a necessary part of every cybersecurity protocol. Any organization or individual would need to have responsibility for any incident or loss of data. Furthermore, it’s more like a backup plan, if somehow the security failed to stop the attack.
Do you really want to understand the concept of blockchain security? Enroll in Certified Blockchain Security Expert (CBSE) course now.
- End-User Education:
Finally, end-user education would help any kind of enterprises to understand the most unpredictable factor – the people, better. Usually, human errors cause most of the security system to fail because it happens from the inside.
In reality, most employees don’t know how to tell the difference between affected programs or to tell which emails contain viruses. That’s why the end user education is really important when it comes to full security for an organization. In this way, people are secured from both inside and outside.
Do You Really Need Cyber Security?
Before you ask this question, you need to know that cybersecurity is a massive threat in 2019 due to the increase in the use of technology. The more you rely on it, the more you have to consider the security for it.
In reality, many seem to think that it’s not that necessary, or they can go about their days without getting any security.
However, it’s not the truth. In the US alone, the average cost of cybercrime is $13 million for organizations. Not only this but the damages per year is expected to reach $6 million by the year 2021!
Yes! It’s a huge amount, and it’s high time and organizations started caring more about the consensuses of cybercrime. That’s why to combat with all the issues and to recognize which the malicious code is, the National Institute of Standards and Technology thinks it’s best to have monitoring networks at all times.
Any cyber-security counters three kinds of threats –
- Cybercrime including a group or a single person that targets a system for disruption or financial gain.
- Cyber-attacks due to political gain or some kind of political motivation. Moreover, mainly, these include information gathering nothing else.
- The cyber terror that uses electronic devices to cause some kind of fear or panic.
Made For All
In reality, cyber security threats will affect any kind of industry, regardless of size. However, the big names have the most targets of all. Furthermore, it’s not only limited to one industry. In reality, many industries such as government, finance, manufacturing, healthcare, supply chain, IoT, and many more have complained of cybercrime.
Some of these are more preferable as they can collect finances or use the data to blackmail people. In other cases, they mostly target businesses that tend to be on a network system to bring out customer data.
However, the issue is, in today’s world, you can’t be off the grid or out of the network. So, protecting your data will be more difficult.
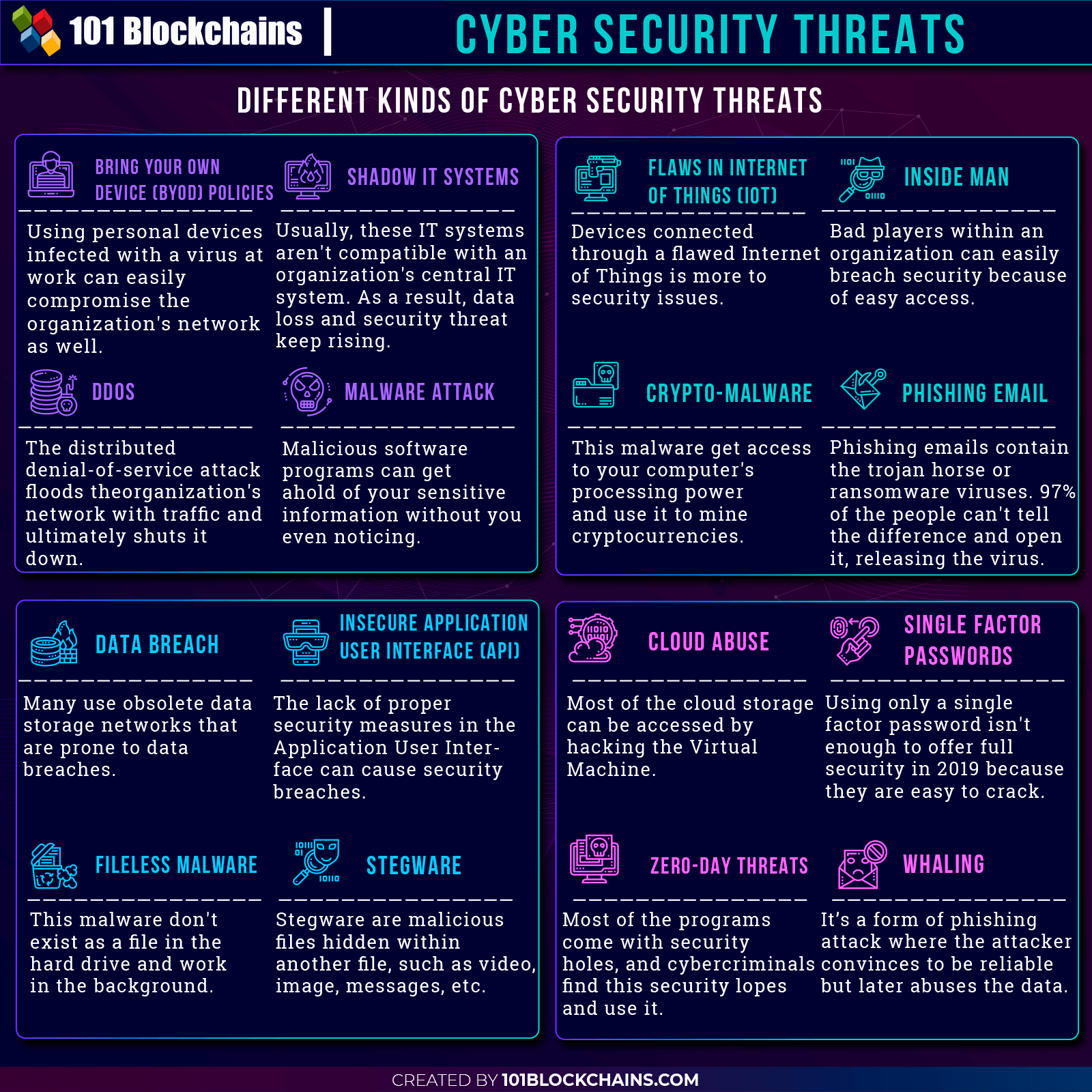
Chapter-2: Different Kinds of Cyber Security Threats
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2019/07/blockchain-cybersecurity.png' alt='Cyber Security Threats='0' /> </a>
-
Data Breach
By the year 2019, many organizations are more than eager to start using cloud data storage as their information storage space. So, many are ditching their old traditional methods of storing all the information and moving on to more secure platforms.
Even though they may sound really safe, they aren’t quite safe as you may think. Issues such as offline backing up data offline oppose to more issues. In reality, the virtual machine on the network can access your files even if it’s offline.
Thus, it can get ahold of the keys, and this results in leaked information. But why does this happen? Well, usually under the same could environment, many applications tend to operate together. As a result, they can access each other’s database without any issues.
The only remedy for this issue is to be very selective while picking your cloud provider. However, still, it might not guarantee 100% safety from data breaches.
-
Insecure Application User Interface
Maybe you are already on a cloud provider. However, you won’t be the only one using the interface, would you? Well, this creates a security hole. In reality, the security of any particular interface would remain solely on the cloud provider.
So, how does the breach happen through the application user interface? Typically when there’s a lack of tight security, it usually comes from the authentication process and encryption. So, the authentication interface isn’t protected enough to keep the hackers out!
In reality, many of the organizations don’t seem to look deeply into what their cloud service provider is offering them. It happens so often, and they pay the price with cyber-attacks.
-
Cloud Abuse
Clouds are abused greatly when it comes to registration for the first time. Let me explain. Let’s say you want to get one of their infrastructures as a service offerings and for that, you need to sing up and provide your credit card information.
After signing up, after a few days, you start to get spam emails and other malicious attacks. Furthermore, you even see your credit card getting bills for services that you never ever even used. This is practically a common scene.
I’m not saying that every cloud provider is the same, or that the providers are in on it. However, the lack of security in the registration process mainly leads to these issues. Unfortunately, the service providers aren’t equipped with great security application to fully control the registration process.
So, as a result, many abuses the cloud environment.
-
Malware Attack
Malware attacks are another cybersecurity threats in 2019 that you need to keep your eye out for. In reality, the malware attack usually refers to the malicious software activities that they do without the owner knowing anything.
Furthermore, there are so many kinds of malware attacks, and most of them happen from any free software programs or files. Also, having a backdated internet security system can lead to malware attacks.
If malware somehow gets into an organizations network through one of the computers, it can cause a great load of havoc.
-
Fileless Malware
These are mainly a type of malware that doesn’t seem to have an existence as files. Furthermore, fileless malware is more dangerous than regular ones as you can’t detect what the affected program or file is.
You can’t find it in your system. In reality, they take up the RAM space and keeps running in the background. However, they are visible once the attackers activate them, and that starts to relay information to the third party.
Many hackers use this system to insert malware in the bank’s network using the ATM. So, once the malware gets into the system, they activate the program and gain total control over it. Furthermore, in other cases, they can also use this type of malware to unload different kinds of malware.
In reality, these are really hard to detect even with internet security software.
-
Crypto-Malware
Well, with the rise of cryptocurrencies in recent years, many hackers now use this new method of hacking. Therefore, with the help of crypto malware, now the hacker can get access to the infected person’s computing power. Furthermore, they use it for mining cryptocurrencies.
So, as soon as your infected browser gets online, the hacker will automatically get access to it and use it to mine cryptocurrencies. However, it’s not directly harmful or hurting you in any way. But it disrupts your computer’s processing power and slows it down.
You’ll see the excess load time and slow performance out of nowhere. And after a short time, your computer will ultimately break down due to excessive mining.
-
Zero-Day Threats
You obviously know by now that all the software isn’t that perfect. In reality, most programs start with security holes knows as vulnerabilities. Furthermore, these loopholes are heavily exploited by hackers. Thus, when the hackers figure out a loophole and exploit it before the developers can fix the issue is a zero-day threat.
So, even if your program was legit or came from good developers, there could be a chance for a hacker to abuse loopholes and deliver other malware using that. Just, imagine that one of your employers opened a file and it launched ransomware into the system.
Can you imagine what the losses would be?
-
Loss of Data
Loss of data can happen for any kind of reason. However, cyber-attacks are on the top priority in that list. Every day many organization face deletion, and alteration in their data without proper authority. Moreover, it could be an unreliable storage facility to be the cause of it.
However, it comes with serious implication for organizations. Losing the data would be getting a huge setback and disruptive for the business line. Furthermore, it can spoil the reputation of your brand; you can lose customers and lose finance.
Here, by cyber-attack, I also mean from within the facility. If you don’t have proper protection or detection method, it will likely affect you.
-
Hacking
Hacking has been around for generations, and now it’s a huge concern for organizations. I can’t say when the trend can truly change; however, it’s not going to be anytime soon, that’s for sure.
Due to the reliability of technology, now the hackers can use the weak points to get into a system. In reality, hacking mainly occurs due to sharing credentials or bad password protection procedures. Furthermore, many people working in organizations don’t know to not share their credentials with web portals.
That’s why when a hacker gets into the employee’s network, the hacker also gets access to the internal network as well. Thus, giving him a jackpot.
-
Single Factor Passwords
Apparently, single factor passwords aren’t enough now to safeguard all your information. In reality, they are extremely easy to hack into. So, it gives the hacker easy access to the data. To deal with the situation, using multi-factor authentication process may help. However, that’s still might not be enough.
-
Inside Man
All the organizations don’t only face outsider threat but insider threats as well. Mainly the employees in every organization are weak points. Furthermore, ex-staffs can also cause serious damage to any organization.
Usually, employees don’t have the proper knowledge to see the loopholes or patch up even if they figure out one. In reality, many can’t even tell apart from a regular email to a malware affected email. So, to deal with it, many train the employees or even monitor their activities online.
However, due to the lack of proper monitoring channel, it continues to be a threat to every organization.
-
Stegware
Mainly these are a type of malware that extends other malware effects. How? Well, hackers tend to use steganography to hide a corrupt file within another file such as video, image, or message. So, it could be in front of your eyes, and you might never assume that it’s infected with malware.
Typically cybercriminals with great development skills can actually craft their very own stegware. However, due to the dark web, many hackers offer kits to build their very own stegware, and so now even amateur hackers can do so.
Thus, many fall victim and can’t even figure out which is the affected file as they’re hidden behind a legitimate one.
-
Flaws in the Internet of Things (IoT)
We used the internet of things heavily over the last few years, and it would be trendier in the future as well. Nowadays, most of the devices are connected through the Internet of things. However, this creates some weak points in the security system.
As much as they are really useful, many people are greatly concerned about using these as well. In reality, most of the internet of things devices bring their very own security issues. Furthermore, the architecture itself is flawed with great weak points.
That’s why the internet of things also needs a secure environment without any loopholes to offer all the features.
-
Shadow IT Systems
These systems are mainly the IT software that doesn’t really go with organizations internal IT network. AS they aren’t supported, it creates a gap of commination or disabling certain features. Furthermore, it’s most prominent in companies that don’t tend to look into any new system before implementing it.
So, when a loss of data happens in one of the IT software, it does not get that much attention and organizations lack in backing them up.
Also, with the unsupported features, no one can tell who gets access to it and who doesn’t. So, it delivers a great option for anyone to abuse. In many cases, most organizations don’t background check before getting the IT resources from vendors. Thus, creating more loopholes.
-
Phishing Email
Phishing emails are emails that contain some kind of Trojan horse or ransomware. Usually, they look like normal emails with some distinguishes. So, when someone from within the company opens this mail, the Trojan horse gets into the system and causes havoc.
These type of emails start the attack right after getting into the system. So, there’s no wait time either or no way of getting rid of it.
According to a recent survey, more than 97% of the people can’t tell the difference between a phishing email and normal email. For this reason, preventive measure is extremely necessary.
-
Whaling
It’s a form of business attack where the cybercriminal manages to convince their targets that they are legitimate. In recent years, whaling happens to rise to be the biggest threat of all. Furthermore, these attackers deem trust in the first stage, and later, when they get access, they abuse the data.
There’s a nearly 136% increase in losses due to whaling between 2016 and 2018. And as it’s a different kind of hacking approach, no internet anti-malware program can help you.
-
Bring Your Own Device (BYOD) Policies
Nowadays, many of the organizations tend to encourage their employees to use their personal devices for the work environment. Furthermore, it also boosts productivity and flexibility. In reality, it might seem like a great policy, but it creates a massive threat for the companies.
For example, no matter how much active security protocols you have, an affected employee device can easily breach your security. There’s no way of knowing whether the employee device is affected or not or no way of offering security for their homes too.
Furthermore, personal devices are easy to hack than organizational networks. So, if the hacker gets ahold of the employee’s device, it can reach your organizations’ firewall in no time. Thus, increasing the overall cyber threat risks.
-
DDOS
Distributed Denial of service attack or DDOS attack is a type of attack that floods the organization’s network with traffic and ultimately shuts it down. Furthermore, they happen to attack from multiple sources that could go up to thousands. Thus, making it hard to track the exact location of the attack.
So, you can’t stop the attack by simple blocking any specific IP address. As a result, the network shuts down, making all the resources unavailable for both the consumer and the organization. To be frank, there’s no specific reason why hackers mainly do this.
However, it could be because of harming the organizations brand or just simply taking credit for taking down a big organization’s network. Needless to say, high profile organization are the main targets of DDOS.
Enroll Now: How to Build Your Career in Enterprise Blockchains
Chapter-3: Can Blockchain Fix Cybersecurity?
Traditional security solutions aren’t capable of handling cyber attacks with an increasing number of complex and cooperating machines. However, blockchain security in the mix can really help to be the comprehensive solution for the issues.
As you can see, the cybersecurity sector is loaded with issues. And more or less a fragile cyber solution isn’t capable of handling all the different kinds of threats. Thus, blockchain can be the most promising solution out there right now.
I mean, think about it. It’s been some time since the technology was introduced first. Even though it did pose a lot of insufficiencies still after the years, it’s now blooming to be a great solution.
Furthermore, it’s already working in multiple organization in different industries such as healthcare, government, supply chain, energy, etc.
So, as a firewall technology, it offers a lot of security protocols. Also, they’ve been gaining a lot of praises from all the industries using it. So, it can easily fend off cyber-attacks.
Blockchain technology is a distributed ledger technology that uses nodes to form the decentralization concept. More so, it also uses a form of mutual consensus to protect the data. For example, if any hacker tried to hack some of the nodes in the network, other nodes can easily use the consensus process to detect who the bad player is.
Furthermore, they can use the method to lock out the compromised nodes and saving the whole network. Moreover, you can see that blockchain security actually uses several strength systems to offer the redundancy and tamperproof republication mainly.
But What Does It Mean?
In many terms, it could mean that hackers may take down a few of the troops, but they can’t take down the overall Blockchain security army. As you can see by troops, I mean few nodes and by the army, I mean all the nodes in the network.
So, with blockchain security on the mix, no industrial operation or information storage is left to depend solely on the single vulnerable system. In reality, blockchain and cybersecurity help it to become more scalable and disruptive.
Furthermore, it means that most security policies, such as flow controls or rotating passwords, would get controlled more diversely. More so, only authorized persons can get access to specific controls. You can try to replicate centrally and then slowly roll it out to other fields.
Moreover, these controls would be used tamper-proofed and by all the nodes on the blockchain and cybersecurity network.
Therefore, as you can see, it forms a self-protecting firewall. Thus, it doesn’t have any single point of failure. Furthermore, there would be no unauthorized access to the network or no accidental changes in the blockchain security network.
So, if you are confused about whether blockchain security can be the solution, I can surely say that it most certainly can. However, many people don’t know what type of blockchain security solution they need as the cybersecurity itself has different types.
So, before picking out the solution, the organizations need to know exactly what type of use cases the blockchain security has.
Want To Know More About Blockchain? Check Out The Blockchain Presentation Right Now!
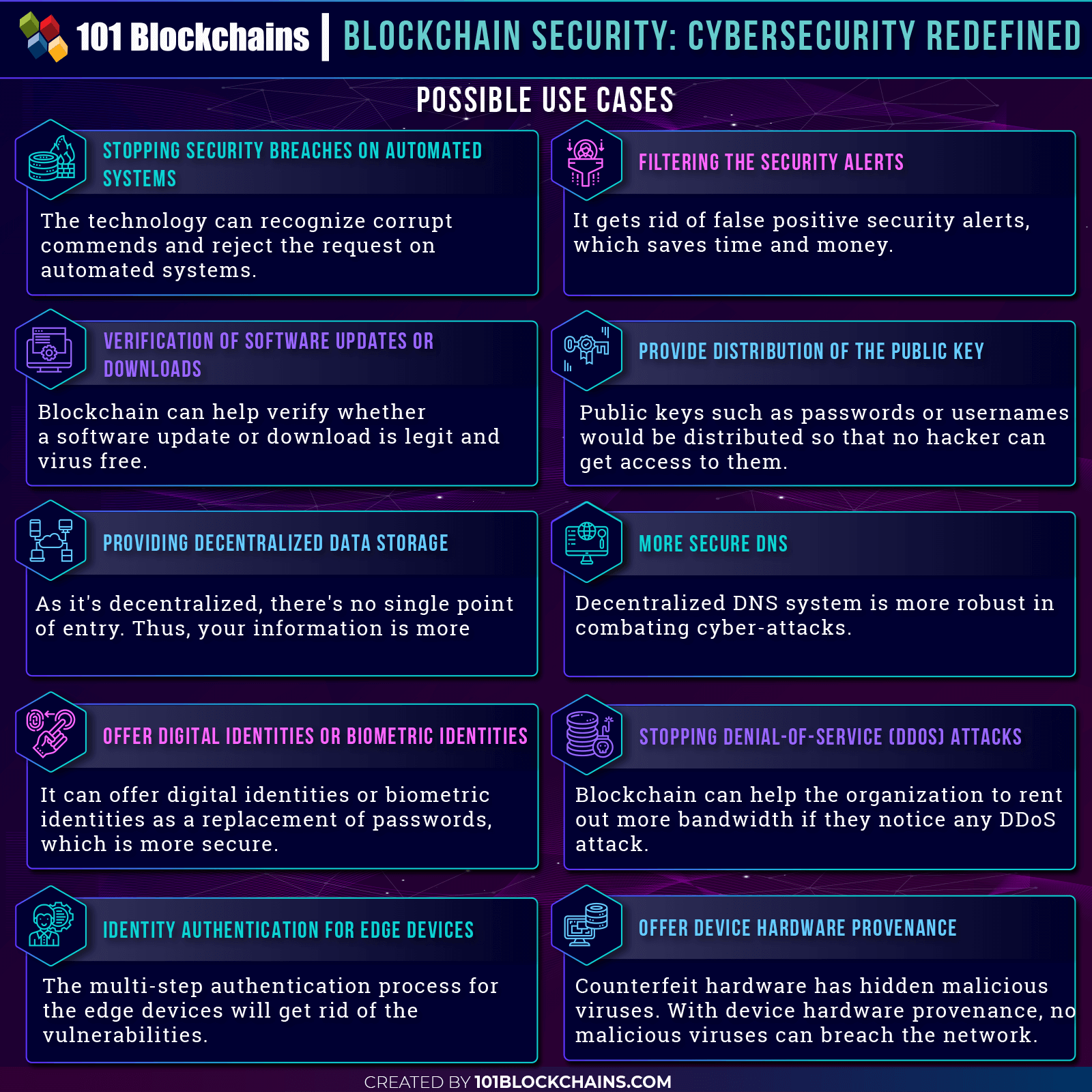
Chapter-4: Blockchain Security: Possible Use Cases
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2019/07/blockchain-security.png' alt='Blockchain Security Use Cases='0' /> </a>
When you look at the statistics of cyber-attacks, you’ll realize how the security protocols are really evolving. Moreover, you’ll also realize how the cyber-attack systems are becoming more and more difficult to handle for the typical security protocols.
From the starting of 2016, every day, the criminals launched 4000 attacks. Furthermore, no matter what people did, it became very clear that the escalating nature exceeded 2015 attacks by 300%. Even in 2015, the attacks were close to 1000 a day; however, it tripled in 2016.
Some of the major hacks also happened in 2016, where 57 million driver and user accounts were compromised in Uber. Furthermore, the same year, 412 million Friend Finder user accounts were compromised as well.
So, you see the stake is high now, and no industry is even safe from the attacks. In reality, hackers are looking constantly for newer targets to corrupt. Thus, even if you have been safe in the last couple of years, it’s not a certainty whether your company will be safe in the future as well.
However, there may be no method that can offer a 100% guarantee. Still, blockchain security is far better than traditional ones. As I said earlier, that blockchain security can really tone it down for you.
Furthermore, considering that blockchain and security network can prevent hackers from getting out sensitive information, I’ll say this is a heck of technology to try out.
However, you may not be so much familiar with the probable blockchain cybersecurity use cases that it can bring to the table. So, now I’ll be digging a little deeper into that spectrum.
Check Out Our Blockchain For Trade Finance Guide Now!
-
Verification of Software Updates or Downloads
Any kind of Trojan horses, worms, and viruses can easily get into the computers in various forms. And most of the time they are extremely difficult even to spot. In the starting of 2016, over 127 million different types of malware got created. To be frank, these are all very difficult to identify without a trained eye.
In fact, many times it comes in the form of a software update or a bogus software download option. Want to what’s more daunting? Every day the AV-TEST institute happens to register 350,000 new types of programs as malware. Furthermore, the Mac OS that seemed so untouchable is now a target of malware.
In reality, just for infecting Mac, there is 49,000 malware, and all of them were created in 2018. Moreover, all these frauds are so expert in hiding their application and software in plain sight that the typical anti-virus protocols can’t seem to find them out in any way.
And instead of you, they are taking home all the revenues that you earned through hard labor. Doesn’t seem fair, does it?
That’s why it’s a necessity now to go with blockchain cybersecurity use cases. Furthermore, blockchain security features are not only capable of figuring out which software is legit and which is not. But blockchain security can also let you know if there’s any malicious update.
How do they do it? Well, in cyber security blockchain technology, you can compare the hash functions of both the developers and the one you are going to download. After you compare these two, you can really verify whether it’s legit or not on the blockchain and security platform.
Thus, it drastically gets rid of the one headache from your list.
Learn More About The History Of Blockchain Now!
-
Stopping Distributed Denial-Of-Service (DDoS) Attacks
Distributed Denial of service attack or DDOS attack is a type of attack that floods the organization’s network with traffic and ultimately shuts it down. Furthermore, they happen to attack from multiple sources that could go up to thousands. Thus, making it hard to track the exact location of the attack.
Usually, these attacks don’t really gain anything like hold the system for any money or getting your personal information. It’s more of like a claiming credit while destroying your business for literally no reason.
Furthermore, a new type of DDoS software is also making it more difficult to handle. In reality, these hide out and play dead until the system is rebooted. Moreover, it can launch the attack over and over again. However, you can’t find out where the source is.
Thus, it’s becoming more and more difficult to manage all the issues or keep up business consistently.
Using it for stopping DDoS attacks is another one of the blockchain cybersecurity use cases. But how will blockchain security solutions really do it? Well, first of all, there needs to be a backup team for saving the network when it comes under fire.
Usually, due to an increased level of traffic, many of the organization’s network shut down. But when the company’s network is under attack, the blockchain, and security network and activates the extra distributed nodes to accommodate more bandwidth.
So, when the bandwidth gets used up, more bandwidth allocation is introduced. Thus, ultimately, the cyber security blockchain technology wins. But you can only use this method of increasing the network using blockchain security and nothing else.
As a result, hackers won’t be able to take down your organization anytime soon.
-
Offer Digital Identities or Biometric Identities
Most of the passwords used online would get a “weak” tag and just waiting to get hacked.
Apparently, single factor passwords aren’t enough now to safeguard all your information. In reality, they are extremely easy to hack into. So, it gives the hacker easy access to the data. To deal with the situation, using multi-factor authentication process may help. However, that’s still might not be enough.
Did you know that according to Facebook, over 600,000 users account gets hacked every day just due to predictable passwords? That’s a lot of numbers! And it’s a security risk for you as well if your organization’s network authentication is based on passwords as well.
In reality, you need to keep changing your passwords frequently to compete safely. However, that leads to more complicated passwords that we can’t keep track of. Moreover, most of the people don’t change their passwords due to the excessive hassle. However, if you keep the same password for long, it becomes predictable.
To help you out in this regard, blockchain cybersecurity use cases is here. Not only blockchain security is capable of safeguarding your passwords, but it can really change the way people get into any system.
With cyber security blockchain technology, you’ll get digital identities or biometric identities as a replacement of passwords.
In reality, digital identities or biometric identities is much safer than passwords. And so, without your biometric key, no other person can really get into your personal documents on the blockchain and security network.
Furthermore, the blockchain security solutions are not only more secure, but it’s easier to use them as well. Nowadays, many companies offer this solution for enterprises as well.
Want to Know More About Blockchain? Check Out Our ultimate guide on Blockchain Fundamental Presentation.
-
Stopping Security Breaches on Automated Systems
The rise of autonomous technologies is opening up new heights for people and organizations. However, it’s also opened up more loopholes for the hackers to get in. In reality, the laid back nature of the organizations or lacking in proper security measures is making the autonomous systems more fragile than ever.
Hacking has been around for generations, and now it’s a huge concern for organizations. There’s no way of knowing whether the trend will ever change or not. But it’s safe to say that it won’t be anytime soon.
Due to the reliability of the automated system, now the hackers can use the weak points to get into a system. In reality, hacking mainly occurs due to sharing credentials or bad password protection procedures.
Furthermore, many people working in organizations don’t have the knowledge not to share their credentials with web portals.
That’s why when a hacker gets into the employee’s network, the hacker also gets access to the internal network as well. Thus, giving him a jackpot.
Therefore, it’s time to move onto blockchain cybersecurity use cases. In reality, the blockchain security solutions are capable of figuring out corrupt and invalid inputs and commands. Using algorithms, the blockchain and security network can determine when a corrupt command tries to enter the network.
More so, the cyber security blockchain technology is so advanced that it can easily stop these without any issues at all. And using that you can easily figure out which of the automated system is compromised and start the recovery process as well.
So, you see that’s how the blockchain security can help out in automated systems.
-
More Secure DNS
Domain Name System or DNS is kind of similar to phone books that helps to determine a website based on the IP address. Mainly these are necessary to help you find the right website when you are looking for it.
However, the issue is that DNS is only partially decentralized. So, any hacker can get access to the connection of the website and IP address and use that to crash at any time. In reality, it leads to a major downfall for the enterprise as they lose their business and have a bad customer impression. So, ultimately, it starts to degrade their brand value as well.
Some of the common methods are to, infect the DNS to redirect the customer to many scam websites. Not to mention every single thing of the website is filled with malware. So, you might open a legit website and get redirected to an infected one, only to get some malware loaded into your device.
It’s a serious issue for enterprises, and it demands more security in this niche.
That’s why blockchain cybersecurity use cases can help out to solve the issue. Well, the solution is to make the DNS a fully decentralized system. So, with cyber security blockchain technology, no hacker will get access to the IP links.
Also, the blockchain security solutions not only will host the DNS system, but it would also offer more security layers for it.
As a result, there are different security protocols at every level making the blockchain and security network a full proof system.
And that’s how the blockchain security can take care of the vulnerabilities of the DNS system.
-
Providing Decentralized Data Storage
If you use centralized storage for keeping all your information, then you are just a sitting duck, waiting to get hacked. In reality, most of the centralized storage is prone to loss of data.
Loss of data can happen for any kind of reason. However, cyber-attacks are on the top priority in that list. Every day many organization face deletion, and alteration in their data without proper authority. Moreover, it could be an unreliable storage facility to be the cause of it.
However, it comes with serious implication for organizations. Losing the data would be getting a huge setback and disruptive for the business line. Furthermore, it can spoil the reputation of your brand; you can lose customers and lose finance.
It makes you think how come these businesses never tried out something else. And every day, the number of storage breaches keeps rising. So, it’s prominent that the centralized database can’t offer the protection in any way.
However, with blockchain cybersecurity use cases, you can really change the ways things work. The network architecture of the blockchain security solutions is decentralized by nature. So, with this new method, you won’t leave any single point of entry in the blockchain security network.
More so, here, instead of a single entry point protecting the information, there are thousands of robust barriers protecting your data. And that is how the blockchain and security network works.
Also, with cyber security blockchain technology, you’ll need interoperability to get the full experience. In any case, the tech does manage to pull it off, whether you doubt it or not.
Excited to know about the fundamentals of Corda Blockchain? Check out our ultimate Corda Blockchain Guide Now!
-
Identity Authentication for Edge Devices
We use edge devices heavily every single day of our lives, and it would be trendier in the future as well. Nowadays, most of the devices are connected through the Internet of things. However, this creates some weak points in the security system.
As much as they are really useful, many people are greatly concerned about using these as well. In reality, most of the edge devices bring their very own security issues. Furthermore, the architecture itself is flawed with great weak points.
Did you know that 41% of all the android devices are vulnerable to extreme Wi-Fi attacks? Not only it will corrupt the phone, but if it’s connected to any kind of site, it will corrupt those too.
In reality, many employees tend to log into their company’s network with the unsecured phone, and that leads to easy access for hackers.
That’s why the edge devices also need a secured environment without any loopholes to offer all the features.
So, you see blockchain cybersecurity use cases, in this case, is highly suitable. It can offer the identity authentication needed for these highly vulnerable edge devices. But how will the blockchain security solve this issue?
Well, first of all, the blockchain and security network will isolate the core network with a multiple-step authentication process. Here, it can use a biometric key or signature that would ensure proper login.
Therefore, the blockchain security solutions can make sure that only the authorized person is entering the system. With the help of the decentralized storage, the cyber security blockchain technology can also store the keys in a safe place.
Furthermore, the network itself can offer digital identities when a company sets it up for the first time.
Enroll Now: Beginner’s Guide to Corda Development
-
Provide Distribution of the Public Key
Even if you rely on passwords or you have to do it until all the systems in the world is fully decentralized, how can blockchain security help in that case? At present, most of the passwords and usernames are saved in centralized databases.
Well, you know by now that these are extremely easy to hack. If somehow the database itself gets hacked, then the hacker just hit the jackpot. You might be thinking what’s the big deal if it gets the password of any social media account or some website that you barely use?
Well, the issue would be when you use the same or similar password for your bank account logins or your healthcare record logins. Moreover, it’s easier to figure out a pattern from seeing ones password. So, even if you think that a single password hack won’t make any difference, in reality, it can.
And this how the hackers get befits from. To stop it, public keys such as passwords or usernames would be distributed so that no hacker can get access to them.
Blockchain cybersecurity use cases will offer a blockchain security network that’s fully decentralized. If you start to store your public key across multiple nodes with full encryption, it becomes difficult for hackers to get access to it.
Just imagine, you divided up the password and encrypted it and distributed all the pieces among many nodes in the blockchain and security network.
So, even if the hacker tries to get access in the cyber security blockchain technology, he can’t know where the pieces really are.
Furthermore, there are plenty of blockchain security solutions for that on the market for you to try out.
Learn About Different Blockchain Business Models To Leverage The Technology Now!
-
Offer Device Hardware Provenance
This is the ear of cyber warfare where cybercriminals use everything in their power to cripple us. In reality, every industry faces theft issues and don’t have proper security to maintain those.
Moreover, many companies snow have counterfeit products as well. These products get into their system without leaving any trace, and people are buying them as legitimate products. More so, the hardware is one of the highest counterfeited niches of all time.
However, the cybercriminals are leveraging this counterfeited hardware for their benefit. Counterfeit hardware has hidden malicious viruses. Yes, you heard right, they insert the viruses in the hardware before supplying it to legitimate industries.
As there’s isn’t any hardware provenance, many organizations don’t know if they are dealing with good products or bad ones. As a result, when an organization gets the devices and plugs them into their network, all hell breaks loose.
Even though you might have a security protocol up and running, viruses form hardware is really difficult to get rid of.
Thus, there needs to be hardware provenance, and blockchain cybersecurity use cases can definitely do that. With device hardware provenance, no malicious viruses can breach the network anymore. Now while manufacturing, the industry can see if the supplier is legitimate or not in the blockchain security network.
With the help of the blockchain and security platform, it can easily figure out the origin of the hardware. It’s one of the many perks of cyber security blockchain technology, and the immutable database helps to keep the information untainted.
There are already several blockchain security solutions out there for this niche specifically.
-
Filtering the Security Alerts
Well, the use of typical cyber security protocols is great. However, with that comes to a lot of costs as well. The issue is when they can spot malware or bad data. However, they also seem to flag legitimate data as the corrupt one.
In reality, the false flagging is so vast in number that it needs more additional administrative costs to figure out which one isn’t and which one is. Thus, it keeps adding up more money instead of reducing it.
These false positive data can lead to issues for both consumer and the company itself. Just with false positive data, it costs enterprises over $1.3 million every year. Moreover, the amount of time wasted is 21,000 hours.
So, it doesn’t only waste the enormous amount of money, but it also wastes time as well.
That’s why with blockchain cybersecurity use cases, you can get the filtered data. Furthermore, the blockchain security alerts would be more accurate without any false positives. The nodes within the blockchain security solutions framework can work as a verifier whether the data is correct or not.
Thus, you will get rid of the extra cost and wasted time for good in cyber security blockchain technology. However, that’s not the only benefit here. Blockchain and security platforms are far less costly than average solutions. So, it’s a win-win for everyone.
Chapter-5: Examples of Blockchain Cybersecurity at Work
-
Santander
Santander uses blockchain security to enhance their international payment services. Apparently, they are the first bank in the United Kingdom to adopt blockchain for security purposes. Furthermore, with the help of blockchain and cybersecurity, they help their customers to pay in South America and Europe using their Santander account.
Also, with the help of Ripple, now the One Pay Fix service is live in Poland, the UK, Brazil, and Spain. We all know how banks internal network is always under constant cyber-attacks. And to make sure that the customers don’t suffer Santander is using blockchain security to safeguard all of their internal networking as well.
-
National Bank of Canada
National Bank of Canada is using blockchain and cybersecurity network for their debt issuance. At present, they are using J.P. Morgan’s Quorum enterprise-Ethereum as the base network. Quorum is an enterprise version of Ethereum with added security protocols to safeguard any organization form cyber-attacks.
And National Bank of Canada is using the blockchain security aspect of it to ensure 100% safety in transactions. Moreover, it’s also working on other projects such as offer a secure channel for supply chain industries.
Anyhow, they recently went through a trial phase of debt issuance, where they issued $150 million one-year debt using the platform.
-
Barclays
Barclays is using blockchain and cybersecurity to offer security in fund transfers. Not only that but they also have a patent for using blockchain security technology. In reality, the primary object of this company is to use it to boost stability and popularity of the currency transfers.
They also are using it for keeping all of their internal databases out of the reach of hackers. On top of that, they also have a patent for blockchain security in KYC processes. So, with the help of it, any bank or financial company can store their personal identification on the blockchain network.
-
Change Healthcare
Change Healthcare is using blockchain and cybersecurity to offer healthcare solutions across the hospitals in the U.S. Not only that, but they also use it for their own security management as well. Furthermore, the company knows how the healthcare industry is falling apart due to the hacks and abuse of the cybercriminals. In reality, it’s an everyday factor that many patient sensitive information gets leaked or hacked from the hospital’s database.
Not to mention, the alteration of data for personal gain is prominent hear. And it’s all because the healthcare industry doesn’t have proper security. That’s why Change Healthcare is not only offering blockchain security solutions, but it’s also using it to monitor their network as well.
-
Health Linkages
Health Linkages is using blockchain security for ensuring a transparent data transfer and audit processes for the healthcare sector. Not only that, but it also uses that to boost the compliances in the industry. In reality, using their platform, you can only share patient data if you have proper credentials.
Also, it lists down all the healthcare events, and which makes decision making clearer for doctors. However, making sure that no hacker or third party gets access to this information is the priority.
At present, they are currently working on a different trial of blockchain and cybersecurity project where the professionals can view patient information in a secure channel.
-
The State of Colorado
The State of Colorado is using blockchain security and thinks that for governmental use cases, they can use it for data protection. Not only that, but the Colorado Senate passed a bill regarding the blockchain risks to secure their storage of records.
Usually, Colorado deal with 6-8 million hacking attempts every day. And many time the hackers were victorious, damages the government structure. For dealing with that, Colorado is using the encryption of blockchain to keep them away from any attempted hacks. And that’s how blockchain security is affecting the governments as well.
-
Australia
Well, the Australian government isn’t that far behind when it comes to using blockchain and cybersecurity to store their governmental documents. In reality, the country recently prioritized the use of blockchain security network for government.
Even though the network is still in the early phases, but still the government officials think that the technology will soon become a really valuable asset.
At present, they are taking technological support from IBM to make the government ecosystem. Also, the federal government thinks that it’s going to be a wonderful addition for future governments as well.
-
Malta
Currently, Malta is using blockchain security to back up their financial sectors. However, government officials are also looking into the security aspect of blockchain. Why? Well, they mainly want to safeguard all their governmental documents. Moreover, they also want to keep all the citizen information away from cybercriminals.
In reality, Malta is more than eager to welcome blockchain in every sector. In fact, they want to become the Blockchain Island. Also, with the increasing cryptocurrency craze in Malta, they have been under the hacker’s target for a very long time.
That’s why the government wants to use blockchain as the security layer for their databases as well.
-
Defense Advanced Research Projects Agency (DARPA)
The Defense Advanced Research Projects Agency or DARPA is really the United States Department of Defense agency that works on technologies for the military. In reality, they mainly develop different emerging technologies for the US military.
However, now that the blockchain technology is one of the emerging techs, DARPA is looking into how it can use it for the security and encryption of data transfers. That’s why they are working on blockchain security based messaging system that can help the military to share the information to any location instantly.
And also to make sure no third party can intersect their message on the blockchain and cybersecurity network.
Check Out The Differences Between Blockchain And Database.
-
Chinese Military
The Chinese Military is now interested in blockchain security to enhance their security protocols within their military and governmental network. Furthermore, they think that blockchain security has the potential to stop foreign adversaries from changing or altering vital military or governmental information.
Usually, they have to deal with a lot of information leaks and alters. And definitely, a country’s military information shouldn’t be on the third party’s hand. It can seriously harm the country.
However, we still don’t know what projects they are working on due to confidentiality reasons. But we do know that they are looking to cover intelligence operation information and communication between officers.
So, you can see how blockchain security is really impacting the biggest sector in the world.
-
Lockheed Martin
Lockheed Martin happens to be the first United States defense contractor that’s using blockchain and cybersecurity to enhance the protocols. Not only that, but it’s also using blockchain security in supply chain risk management, engineering systems, and software development.
It wants to make sure that every single of these fields have super tight security. In reality, the company is taking technological support from Guardtime.
Another possible reason for it to choose the blockchain security network is to make sure all development of weaponry stays safe and doesn’t fall in the wrong hands because weaponry development is also a vital part within a country and government.
-
Flex and Rockwell Automation
Flex is the supply chain company that’s using blockchain technology for various reasons, and one of them is security. Not only Flex but another hardware company Rockwell Automation is also using blockchain security to offer more secure infrastructure to their manufacturing and shipping process.
At present, both of them took technological support from Cisco. In reality, as part of the trusted IoT Alliance, Cisco is more than eager to integrate blockchain with IoT devices.
More so they think, IoT and blockchain actually pair really well.
-
The US Department of Energy
The US Department of Energy is working with Guardtime to ensure a fully secured network for the distributed energy resources at the power grids edge. Here, by power grids edge, they mean the intersection where the power grid splits to other customers and distributed networks.
Furthermore, they want to stop any misusage of the energy before it splits into other networks. Apparently, the project is called Cybersecurity for Energy Delivery Systems under the Obama realm.
Moreover, using the blockchain to support the system would not only help them fight off third-party attacks but also to ensure more reliability on the infrastructure.
-
Ethical
Ethical is currently using blockchain security for their audit trail protection. Moreover, they are working with Guardtime to ensure full security of the audit trails. In reality, every time an operation gets done, it gets added to the database. Moreover, for each record, a new KSI signature is introduced.
What Ethical does here is store the signature as a proof of evidence? IF the signature is present in the database, then it’s proof that authorship, time or integrity of the audit is still intact. Anyhow, the evidenced gets register into the Guardtime blockchain network for future use.
To ensure that nothing was touched, the company can validate using the signature with the evidenced in the database.
Why Don’t You Check Out Our Hyperledger Blockchain Guide?
-
UK Energy Sector
UK Energy Sector is looking into blockchain security, and for that, they are currently considering Guardtime’s technology. That’s why to understand the concept of blockchain security better; the sector is currently taking cyber exercises from them.
All of the exercises included in the energy environment has different environments, scenario, and real-life simulation to understand how the whole thing really works. However, at present, the primary goal was to help the participants detect the attack, stop it from spreading and recover from it.
Well, needless to say, the exercises were successful, and the UK energy sector got a taste of blockchain power. However, we still don’t know if they’ll implement the tech or not.
-
UK Civil Nuclear Sector
Another huge sector looking into blockchain security is the UK Civil Nuclear Sector. In reality, the nuclear sector needs to have full proof security measures if they want to fend off all the attacks they face every day.
That’s why they are working with Guardtime to understand better the consequences of using technology. At present, Guardtime showed them a real-life cyber-attack on a nuclear plant and how they can defend it.
It seems like it was a huge success. Even though the Nuclear sector is more than eager to work with blockchain, we still don’t know if they have any active project or not.
-
Danieli
Danieli is taking blockchain security solution form Naoris. If you haven’t heard about Danieli, let me tell you just a little bit. Danieli is one of the largest steel suppliers in the industry. As Danilei is one of the blue-chip companies, it’s absolutely necessary for it to get protection for all the client and sensitive information.
At their current status, every single of their employee devices can act as a pathway to their network. So, to make sure that they don’t face any serious cyber consequences, they asked Naoris for blockchain security just for their data servers worldwide.
The project is still ongoing at this stage.
-
Estonian Ministry of Defense
The Estonian Ministry of Defense granted a contract for Guardtime on blockchain security. Actually, they want to develop the next generation of NATO cyber range for the government. In reality, the new design will unlock a lot of features such as electronic warfare, intelligence, mission refinement capabilities, cyber securities, and many more.
So, to make sure everything is on the spot, it needs to have a full-proof cyber backup. And that’s why they’re using blockchain security for that.
If you want to learn more about the challenges associated with blockchain adoption, read out this article: Blockchain Adoption Challenges
Chapter-6: Ending Note
Cybersecurity has been a mess for quite some time now. Mainly right after the malware bloom in 2016, many organizations face a massive amount of losses every year just because of cybercrimes.
However, as you can see, blockchain security is more than capable of handling all the security threat all on its own. I can’t say that it’s a full proof technology. However, judging how other security protocols are working, blockchain is far off to a good start. So, it’s definitely worth looking into.
![Blockchain Security: Premium Protection For Enterprises [UPDATED] blockchain security](png/blockchain-security-premium-protection-for-enterprises-702x336.png)

1 Comment
Wow this blog is very nice