Cryptographic hashing has been an integral part of the cybersecurity spectrum. In fact, it is widely used in different technologies including Bitcoin and other cryptocurrency protocols.
In this article, we will go through hashing in cryptocurrency where we learn about cryptographic hashes, their examples, history, and so on.
The article is aimed at those that want to learn a more technical outlook on the subject. However, don’t be afraid if you are not technical as we will try to simplify the concept in the best possible way.
Cryptography has always been at the core of computer science. Without it, we will never be able to have secure communication or information sharing. It is best defined as the method to protect information.
Want to become a Cryptocurrency expert? Enroll Now in Cryptocurrency Fundamentals Course
What is Cryptographic Hashing?
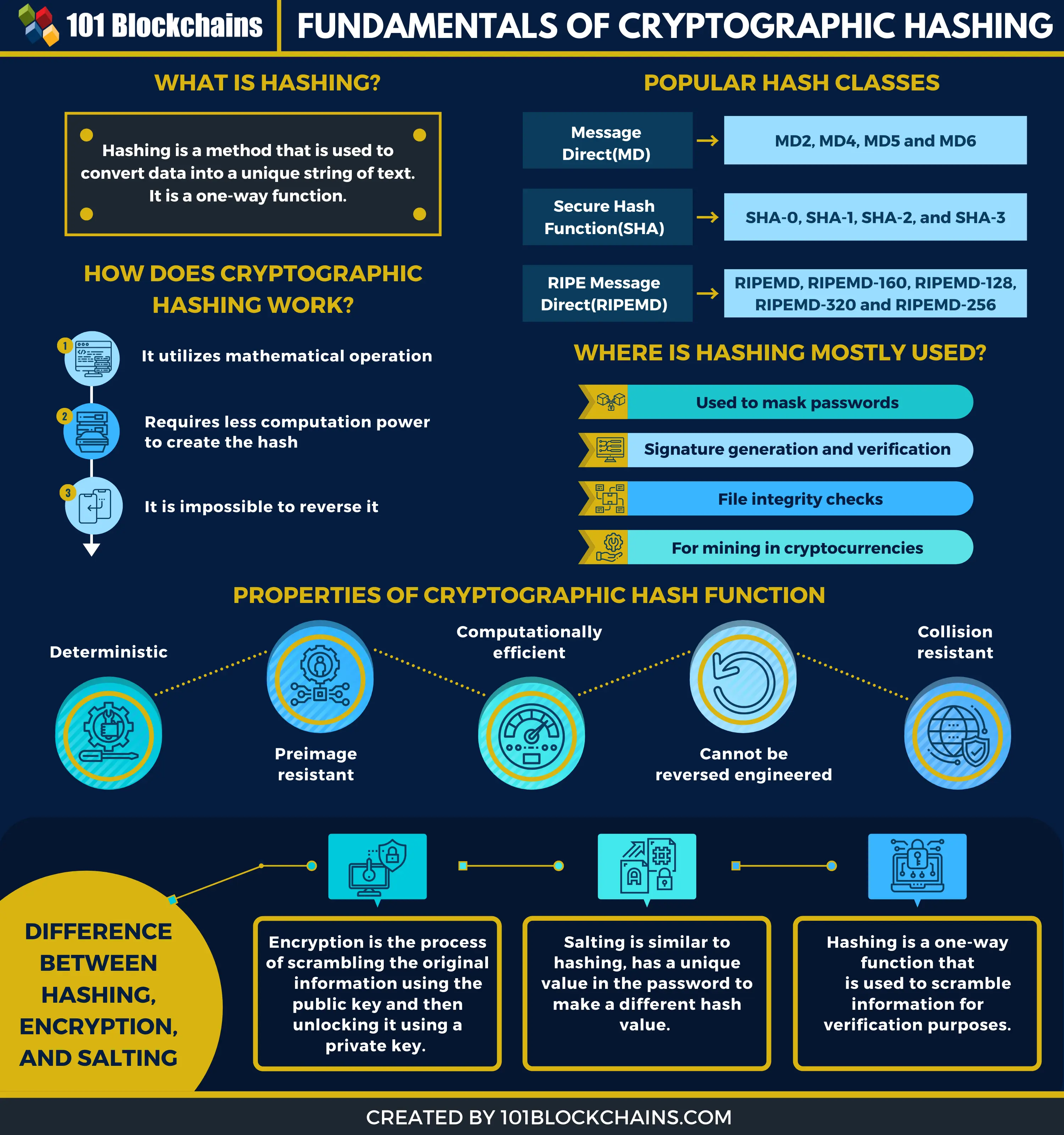
In cryptography, hashing is a method that is used to convert data into a unique string of text. The data is transformed into a very efficient method where the data is hashed in a matter of seconds. Also, there is no limitation on the type of data or its size — hashing works on all of them.
So, what makes hashing so popular and unique? It is because it cannot be reversed!
Yes, it is a one-way function(cryptographic hash function) and it is designed to work like that only.
In a one-way function, the data, once put into the hashing algorithm, output a unique string. However, the unique string cannot be used to decipher the original data by putting it back to the hashing function. This sort of usefulness and feature makes cryptographic hashing so beneficial in protecting information and data.
Also, check out
There is one more feature that applies to the hash method. Any given piece of data will give the same hash output.
These features make it very useful in cryptocurrencies such as bitcoin.
How Does Hashing Work?
To better understand hashing, we also need to learn how it works. Hashing is a mathematical operation that takes less computational power to perform. However, the computational power required to reverse is costly and hence cannot be done by the current generation of computers.
However, quantum computers can reverse computer hashing. But, there are already hashing methods that are quantum resistant.
For hashing purposes, there are plenty of algorithms used. This includes the following.
- Message Direct (MD5)
- Secure Hash Function (SHA1)
- Secure Hash Function (SHA-256)
Not all hashing functions are 100% secure. For instance, SHA1 is easy to crack and hence is not advised for practical purpose usage. One of the most common hashing functions that are used includes MD5 and SHA-256.
MD5 is mostly used for verifying downloaded files. So, if you download a file, then you can compute its checksum using the checksum calculator. If the hash string matches with the string of what the downloader has provided, that means that the download is done correctly without any file corruption. In short, it verifies the integrity of the file.
Where is Hashing Mostly Used?
Hashing is mostly used for passwords. Let’s take an example to understand it.
When creating an email account, your email provider will ask you the email address and password. Clearly, they do not save the email and password in simple plain text. If they do, then they are compromising the privacy and security of your information. To make sure that it is hard to decipher that information, they use the hash function on your password so that even anyone internally working at the email provider cannot decipher it.
So, if you try to log in next time, the hash function deciphers it and matches the saved one and hence grants you access to your email.
Other usages include signature generation and verification and file integrity checks.
There are, of course, other hashing applications out there. Another most popular usage of hashing is cryptocurrencies, which we discuss below.
How Hashing is Utilized in Cryptocurrencies
Hashing is mostly utilized in cryptocurrencies for mining purposes. So, in Bitcoin, mining is a process of verifying SHA-256 hashing functions. This means that hashing can be used to write new transactions, reference them back to the previous block, and timestamp them
The network is said to reach a consensus when a new block is added to the blockchain. By doing so, it validates the transactions contained in the block. Also, the addition makes it impossible for anyone to reverse it. All of these are possible because of hashing and that’s why it is used to maintain blockchain integrity.
Bitcoin uses the Proof-of-Work consensus method which in return uses SHA-256 one-way hash function.
Hashing Function Example
Now, let’s take a look at an example of a cryptographic hash function.
To make it easier for us and you, we are going to use the online available SHA-256 tools.
Here is the link for it: SHA256 Online
Now, if you type 101Blockchains as input, it will give the following output.
Input: 101Blockchains.com
Output: fbffd63a60374a31aa9811cbc80b577e23925a5874e86a17f712bab874f33ac9
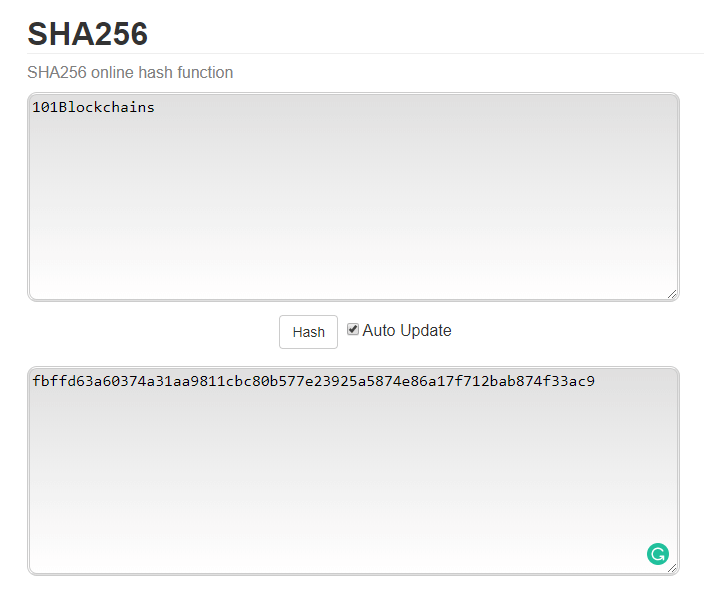
Using SHA256 Hash Function
Now, if you put a simple, “Hello World” as input, it will give the following output.
Input: Hello World
Output: a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e
Among both the outputs, you will see that both the output values are of the same length, i.e., 256 bits, i.e., 64 characters in length.
Now, let’s input 101blockchain into the input. Notice that we removed the “s” from 101Blockchains that was used for generating the first hash.
Input: 101Blockchain
Output: c4d67db72f3d18eaca2e8e8498271de353d25874e4448be4887f2563576c6fe8
If you compare it with our first hash output then you will see a huge difference even when we only removed one letter from the input.
So, what we learned from the example? Let’s summarize below.
- All outputs are of the same length
- Small changes in the input result in completely different outputs
- It is not possible to reverse outputs into inputs.
Properties of Cryptographic Hash Function
To better understand cryptographic hashing or hashing in general, let’s go through the properties of the cryptographic hash function.
Deterministic
Cryptographic hash functions are known to be deterministic. This means that for a given input, the output will be the same. In more simple terms, if you put the same input through the hash function for the hundredth time, the output will be the same in all the cases.
The deterministic property is important as it enables the concept of a one-way function. If it didn’t work that way, then it would be impossible to use it for hashing information. Also, a random output for the same input can make the whole process useless.
Pre-Image Resistant
The cryptographic hash function is pre-image resistant which means that the hash value once generated doesn’t reveal anything about the input.
This is an important feature as it gives the much important.
Computationally Efficient
Hash functions are computationally efficient. This means that regardless of how long and complex the input is, it will generate the hash output quickly. The efficiency is welcome for services that want to use a hash function to store sensitive information. However, it is only computationally efficient one way, i.e., from input to output. As it is not reversible, it is not possible for any computer to reverse engineer it.
But, if you want to talk about numbers, it can take any modern computer years for guessing the input from a given hash value. Also, with modern computers getting powerful by each passing day, the hash functions are becoming more efficient than ever.
Cannot be Reversed Engineered
Hash functions cannot be reversed. This means that it is secure. As you should know that cryptographic hash functions are created with a premise of non-reversible functions. The mathematical equations and process that is used to create the output is simplified and cannot be reversed. In technical terms, the hash function doesn’t support the inverse operation.
Collision Resistant
Collision resistance is the final property that we are going to discuss. This property ensures that no two different inputs produce the same output.
As you should know by now, that the input can be of any length. By this definition, the input can be of infinite numbers. Now, the output, which is a fixed-length, needs to be different every time. The limitation of fixed length also means that the outputs are of finite numbers — even though the finite number is of huge value. This poses a mathematical challenge to separate the outputs for every input out there.
The good news is that most of the popular hash functions are collision-resistant.
Popular Hash Classes – List of Hashing Algorithms
This leads us to our next section, where we discuss popular hash classes. We will list three hash classes that are quite popular among the cryptography sphere.
- Message Digest (MD)
- Secure Hash Function (SHF)
- RIPE Message Direct (RIPEMD)
Let’s go through them one by one.
Message Digest(MD)
Message Digest is a family of hash functions that are used throughout the history of the internet.
The family consists of hash functions such as MD2, MD4, MD6, and most popular MD5. All the MD hash functions are 128-bit hash functions which means the digest sizes are 128 bit.
As we discussed earlier, the MD5 digest hash functions are used by software providers to check the integrity of the files downloaded by the users through file servers. To make it work, the provider gives the downloader access to MD5 checksum for the files. To check the integrity of the file, an MD5 checksum is used that computes the checksum and then cross-checked with the provided hash value. If the value is different than the integrity check of the said file has failed, and the user needs to either download the whole or part of the file.
MD5 is not as secure as other hashing functions. In 2004, an analytical attack was done on the hash function which was performed in just one hour. It was done using a computer cluster. This made MD not so useful for securing information and hence is used for tasks such as verifying file’s integrity.
If you are interested in learning more about MD5, then check out the Wiki page for MD5 — MD5.
Secure Hash Function(SHA)
Secure Hash Functions are another family of hash functions that are quite popular. It was developed and published by the National Institute of Standards and Technology(NIST). They released four versions of SHA including SHA-0, SHA-1, SHA-2, and SHA-3.
As you should have guessed, the later versions rectify some issues or weaknesses with the older versions of SHA. For instance, SHA-1 was released after the SHA-0 weakness was found. SHA-1 was released in 1995.
SHA-1 made its own name once it was released. It was used by diverse applications at that time including the Secure Socket Layer(SSL).
However, with time, exploiters also found about SHA-1 collisions which made it useless. NIST came up with their SHA-2 family of secure hash functions which employed four SHA variants including SHA-256, SHA-224, SHA-512, and SHA-384. In these four variants, two were the core including SHA-256 and SHA-512. The difference between them is that SHA-512 used 64-byte words whereas the SHA-256 used only 32-byte words.
The SHA-2 family of hash functions is still widely used. However, there was also SHA-3 which was devised and released by non-NSA designers during a public competition in 2012. It was earlier known as Keccak. The benefits of Keccak included better attack resistance and efficient performance.
RIPE Message Direct(RIPEMD)
RIPE Message Direct(RIPEMD) is a family of hash functions released in 1992. Also, RIPE stands for RACE Integrity Primitives Evaluations.
It is designed and managed by the open research community. Among the family, there are five functions including RIPEMD, RIPEMD-160, RIPEMD-128, RIPEMD-320, and RIPEMD-256. However, the most commonly used function is RIPEMD-160.
The design of RIPEMD is based on Message Direct.
Difference between Hashing, Encryption, and Salting
In this section, we will briefly go through the difference between hashing, encryption and salting.
Let’s get started with encryption.
Encryption is the process of scrambling the original information using the public key and then unlocking it using a private key. It is a two-way function.
Hashing, on the other hand, is a one-way function that is used to scramble information for verification purposes.
The last term is “Salting”.
Salting is similar to hashing, but here a unique value is added to the password to make a different hash value. Here the salt value needs to be unique and remain hidden.
Conclusion
This leads us to the end of our Hashing in Cryptography. We tried to understand hashing in-and-out by first learning about what it has to offer and then quickly learning how it works, its types, and so on!
As you can see there are plenty of use cases for hashing including cryptocurrency, password protection, signature verification, and so on. Even though hashing is unique in its own way, its effectiveness in protecting information is diminishing with each passing day, thanks to powerful computers across the world.
The researchers are also working towards maintaining the status quo by releasing a more powerful hashing function that is quantum-resistant and can withstand the progression of computation power across the world.
So, what do you think about hashing? Comment below and let us know.