Many of the industries are now implementing blockchain solutions to secure their place in the changing times. However, as other companies are eager to learn about blockchain, many are often confused over how blockchain works. Thus, because of the complex nature, even though many want to implement it, they are unable to fully grasp whether it would be a better option or not.
Blockchain being completely a new system does have a unique way to offer decentralization. That’s why in this guide of how does blockchain work will cover everything related to it. So, just grab a cup of coffee and let the reading begin!
Want to learn more about the Blockchain? Enroll Now: Certified Enterprise Blockchain Professional
How Does Blockchain Work Simply Explained
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2019/12/HOW-DOES-BLOCKCHAIN-WORK.png' alt='HOW DOES BLOCKCHAIN WORK='0' /> </a>
Well, let’s start off with the basics. Before you jump into the process, you need to take note of these critical features of blockchain.
Blockchain will store any kind of data exchange on the platform. So, it’s like a ledger system, where every data exchange has a spot in the log. More so, the data exchanges in the system are called transactions. Once the transaction is verified, it gets a place in the ledger system as a block.
Once it gets on the ledger, no one can delete or alter it in any way.
In reality, blockchain uses a peer-to-peer distributed network, which will ensure the decentralized nature of the technology. Every device that connects to the network is considered a node. Also, to understand “how does blockchain work,” you need to understand the concept of “key.”
This is the basis of technology. Furthermore, the keys offer security on the network. For this, a user on the network will generate key pairs known as private and public keys.
Once you start using the keys, you end up with a unique credential that no one can get access to.
Anyhow, you’ll have to store the private key in a secure place because you’ll use this key to sign or perform any action on the network. On the other hand, other users will use your public key to find you on the system.
For example, imagine your public key as your bank account and private key as your signature that you can use to send or withdraw money. That’s why it’s necessary for you to keep the key as safe as possible.
In reality, if anyone gets access to your private key, they can easily misuse all your assets on the network.
How Does Blockchain Work: The Process
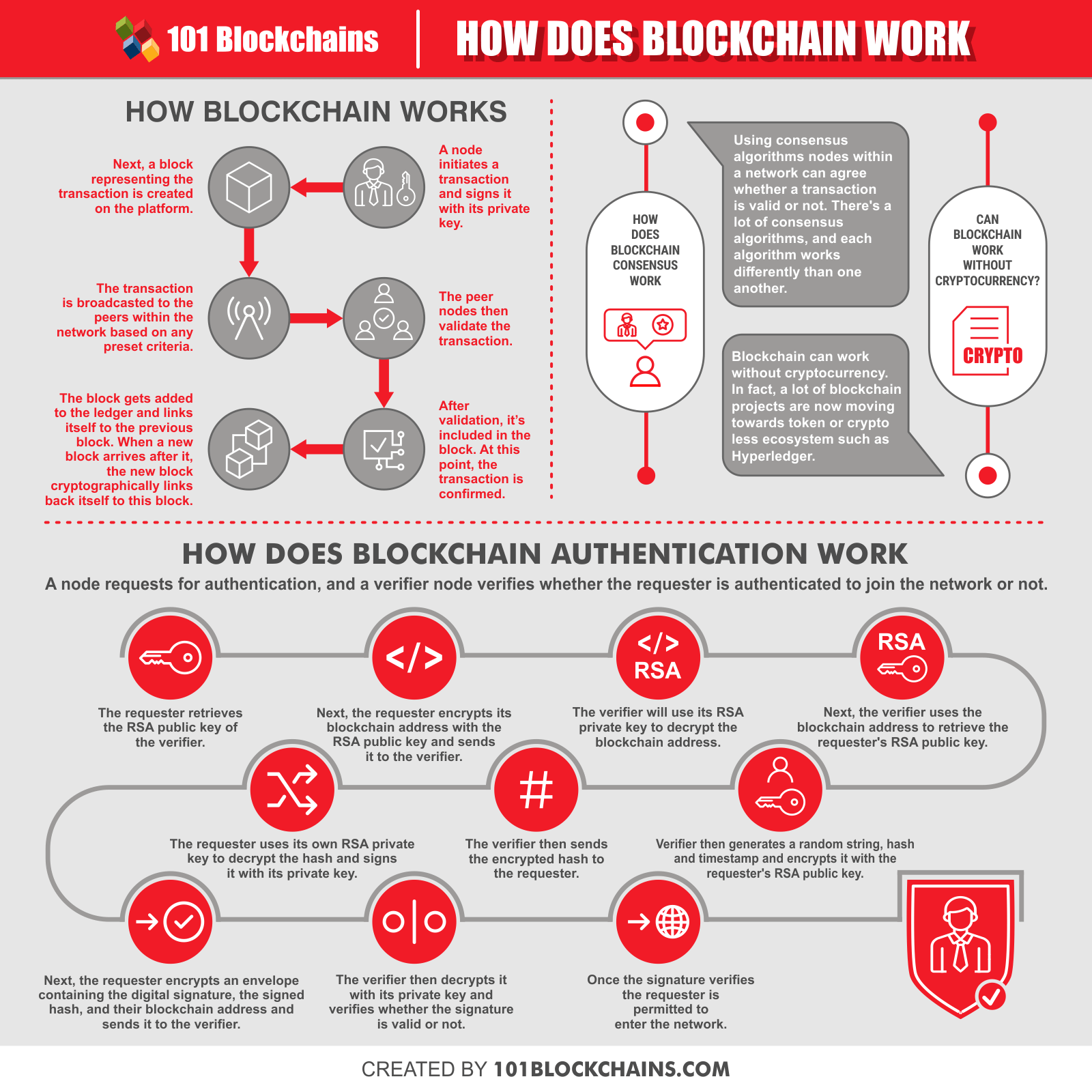
Firstly, a user or a node will initiate a transaction signing it with its private key. Basically, the private key will generate a unique digital signature and make sure that no one can alter it. In reality, if anyone tries to modify the transaction information, the digital signature will change drastically, and no one will be able to verify it. Therefore, it will be dismissed.
After that, the transaction will get broadcasted to the verifying nodes. Basically, here, the blockchain platform can use different methods to verify whether the transaction is valid or not. There methods or algorithms are called consensus algorithm.
Anyhow, once the nodes verify that the transaction is authentic, it will get a place in the ledger. Also, it will contain a timestamp and a unique ID to secure it further from any alteration.
The block will then link up to the previous block, and then a new block will form a link with this block and so on. And this way, it creates a chain of blocks, thus the name blockchain.
How Secure Is The Technology?
Now, you know how does blockchain work, but is the working process secure enough to integrate into the enterprise environment? Well, there’s definitely no network on the internet that’s ‘unhackable.’ But blockchain does offer the highest level of security compared to any other technologies out there.
Blockchain works in a different method, not like the traditional centralized system. So, if you want to hack it, you would have to hack all the devices connected to it. Obviously, it’s a loss project and quite complicated, and that’s why it’s secured.
In reality, hackers would need a tremendous amount of resources to hack a blockchain platform, which will eventually be more costly than the gain itself.
Let’s move on to the next part in this how does blockchain work guide.
There are many young aspirants who want to become a certified enterprise blockchain architect. if you also want to become one, enroll now: Certified Enterprise Blockchain Architect (CEBA)
How Does Blockchain Consensus Work
You already know by now that consensus is a method of reaching an agreement. Basically, it’s a form of how individuals on the network can reach a resolution even though minorities may not like it.
In reality, the consensus is one of the core priorities of a blockchain because, without it, thousands of nodes can never come to an agreement. These models exist to create fairness and equality among all the participants.
However, there’s no one way to reach a consensus within a system. In reality, there are lots of algorithms that various blockchain platforms use. Obviously, every single one of them works differently and comes with its own set of flaws.
So, if you are wondering how does blockchain consensus work, you have to know about each one of them separately to understand.
Proof of Work
It’s one of the popular and first consensus algorithms introduced in the blockchain. Here, nodes are called miners, and they will solve complex mathematical issues with help from their device’s computational power to verify the blocks.
Delayed Proof of Work
Here, some notary nodes will add up data from one blockchain platform to another and secure the power of hashing. Both of the blockchain networks may use PoS or PoW to reach consensus.
Proof of Stake
Proof of stake allows you to take part in the consensus in terms of how much coins you staked in the network. If you have more coins, your possibility of mining a block will increase.
Delegated Proof of Stake
In this one, there’s a concept of delegates and witnesses. Each node is chosen using voting. Witnesses on the platform are responsible for validating the transactions. On the other hand, delegates can change the parameters of the system. Anyhow, all the nodes taking part in consensus will get paid.
Leased Proof of Stake
In leased proof of stake, the smallholders can take part in consensus. As the previous PoS won’t let them stake their coins in the network, it creates an unfair environment. That’s why LPoS offers more fairground.
Proof of Stake Velocity
Proof of stake velocity offers an extra incentive to keep the users from staking into the network. Here, you can earn more if you maintain an active wallet. This means the users who aren’t active quite often won’t get the extra payment for validating a block.
Proof of Elapsed Time
All the nodes have to wait for a certain amount of time before they can participate in consensus. The time limit is chosen randomly. Thus, you can only create a block when you finish the wait time. There’s no way to bypass it, as the system tracks if the node waited or not.
Practical Byzantine Fault Tolerance
Practical Byzantine Fault Tolerance gets rid of the compromised node issue. So, before any node can harm the network, it assumes the possibility of failure. In reality, the system gets information from other nodes as soon as a node is compromised to dismiss that node.
Simplified Byzantine Fault Tolerance
Here, the transactions are validated in a batch. More so, the block generator collects all the transactions and groups them accordingly and then gets them into one block. A validator then has to validate the whole block to verify the transactions.
Delegated Byzantine Fault Tolerance
Here, the leader of the nodes is called a delegate, and it has limited power. If the leader tries to manipulate the network, another delegate will replace that node. More so, other nodes can disagree with the delegate and can change their leader accordingly.
Federated Byzantine Agreement
Here, all the general nodes get their own separate blockchain to run. And before any node can request for a transaction, that node needs to be verified and known from the start. Also, here, a node can choose who to trust on the network.
Proof of Activity
It’s a combination of PoW and PoS. Here, the miners pre-mine a block template rather than a complete one. Later, a validator validates the remaining block. In reality, the more stake a validator has in the network, the more valid his/her validation would be.
Proof of Authority
Here, the nodes participating in consensus will stake their reputation. Basically, the validating nodes are selected based on their true identities. Additionally, the validators have to invest money and their reputation to earn their place on the platform.
Proof of Reputation
It’s quite similar to Proof of Authority; however, a validator needs to have a good reputation to participate in the consensus. More so, if they try to cheat the network, they would face severe consequences.
Proof of History
Here, the system creates significant events on the network. A node then can validate the transaction based on whether the transaction happened before or after that event.
Proof of Importance
Here, the blockchain work keeping a score of the importance. The more coins a user has, the higher his/her score will be. Once they are eligible for participating, they can harvest a block. Additionally, if you harvest more, your importance score will increase.
Proof of Capacity
Users would use their available hard drive capacity to select mining rights instead of using computational power. So, the larger your hard drive would be, the more you can validate blocks.
Proof of Burn
Here, the blockchain works by burning coins to keep the network stable. So, the users would send some of their coins to an eater address and burn them so that they can participate in consensus.
Proof of Weight
Instead of only relying on how many coins you staked, the system stakes into other factors into account to weigh in. So, even if you have fewer coins, you may still get to participate in consensus.
Now you know how does blockchain consensus work. Let’s move on to the next phase in this how does blockchain work guide.
Not sure how to build a career in enterprise blockchains? Enroll Now: How to Build Your Career in Enterprise Blockchains
Can Blockchain Work Without Cryptocurrency?
Blockchain is associated with cryptocurrencies form the very start. That’s why many of you might think that blockchain can’t work without cryptocurrency. But blockchain can work without cryptocurrency.
In fact, there are already many platforms that don’t have any native tokens or coins. A lot of blockchain projects are now moving towards token or crypto less ecosystem. For example, Hyperledger is an enterprise blockchain platform that doesn’t have any native tokens to fuel the network.
The token actually varies significantly based on how blockchain works.
Cryptocurrencies Are Predicted To Fail
Cryptocurrencies are mostly suited for public platforms as they need some form of an incentive program to keep the users taking part in consensus. However, when it comes to enterprise platforms, they go with mostly permissioned or private ones.
As a result, they don’t need a coin or token to encourage nodes to participate in consensus. More so, cryptocurrencies are actually quite unstable for the economy. In reality, a volatile asset isn’t suited for real-life use cases.
Also, having a token in the system attracts hackers, as well. That’s why experts are predicting that cryptocurrencies will soon fail. So, it’s quite logical to move on to blockchain that can work without cryptocurrency.
Governments or other sectors are interested in taking advantage of the underlying use case of the technology, not a token-based architecture. Maybe cryptocurrencies can emerge in the future when the world is ready for the digital money system.
But at present, it doesn’t seem like a possibility. And so, for your blockchain implementation, you should also focus on a blockchain that can work without cryptocurrency.
How Does Blockchain App Work
With distributed ledger technology rising in the market, you must have noticed a lot of decentralized applications, as well. Basically, these decentralized applications are blockchain apps. However, you might wonder how does blockchain app work?
So, how does blockchain app work? In reality, these applications run on the same principles as any other blockchain platform.
These practically have no central point of failure. If you compare them to centralized systems, then blockchain does work in a more reliable way. More so, it will use a decentralized database to store all the information and use decentralized computing power to work.
Additionally, these also use decentralized consensus mechanisms that I outlined in the previous section. Typically, most of the applications use a power-efficient consensus mechanism to reach agreement among the users. A dApp that lags down your computer’s performance won’t reach popularity in the market.
Another fascinating fact about the blockchain app is that the source code of these applications is open for all. The decentralized nature of the model required everyone on the network to get access to it. Also, the user has to verify what kind of app they are using to prevent any malware or protect other users’ information.
Most of the blockchain app work by using some form of token or coin. Basically, it helps to fuel the model and maintain their consensus mechanism. Also, most of the apps offer users a way to exchange value, and thus, digital token or coins are necessary.
Anyhow, let’s move on to the next part in this how does blockchain work guide.
How Does Blockchain Authentication Work
You can use blockchain-based authentication in a lot of industries. In reality, any industry that uses the Internet of things (IoT) will need some form of authentication to offer security.
And that’s where the blockchain-based authentication can shine.
In reality, the feature does offer a lot of advantages –
- Both the decryption and signing keys will stay on the device.
- Encryption and verification keys will get stored on the blockchain platform.
- The process offers protection against any kind of cyber-attacks such as replay, man-in-the-middle, phishing, etc.
However, how does blockchain authentication work seems to a popular question among the newbies. So, let’s figure out how does blockchain authentication work in this guide.
Onboarding A New User
Here, a user can be anyone from an individual to a company or a device. To get the user into the system for the first time, the user would need his/her name, IMEI number, CIN, IP address, account number, etc. The requirements can vary depending on the platform or the company.
Additionally, the user also needs to submit a description of himself /herself.
In return, the blockchain will give them –
- Blockchain Address
- A private key
- A public key
- Relevant transaction ID
- RSA public key
- RSA private key
Among these, some will automatically get published on the network –
- User’s identification
- User’s description
- The public key
- Blockchain address
- RSA public key
However, the newly created private key and RSA private key will not get published.
Authentication Process
While onboarding a new user, the system generates a lot of keys and addresses to help identify the user later on. Now that you know about those let’s see how does blockchain authentication work.
A node requests for authentication, and a verifier node verifies whether the requester is authenticated to join the network or not. For example, here, the requesting node is John, and the verifier node is x company.
- Step-1:
John retrieves the RSA public key of the x company using the company’s blockchain address as the parameter.
- Step-2:
Next, John encrypts his blockchain address with the RSA public key and sends it to the x company.
- Step-3:
The x company will use its RSA private key along with the encrypted file to decrypt the blockchain address.
- Step-4:
Next, the x company uses the blockchain address as a parameter and retrieves John’s RSA public key.
- Step-5:
The x company then generates a 512-character random string and hash and current timestamp and encrypts it with John’s RSA public key. In the meantime, the hash and current timestamp are stored in the company’s ledger system.
- Step-6:
The x company then sends the encrypted hash to John.
- Step-7:
John uses his own RSA private key to decrypt the hash. For this, he uses the encrypted data along with the RSA key as parameters. Later, he uses his private key to sign the hash and get a unique digital signature as the output.
- Step-8:
Next, John encrypts an envelope containing the digital signature, the signed hash, and the blockchain address and sends it to the x company.
- Step-9:
The x company then decrypts it with its RSA private key and verifies whether the signature is valid or not. For this, the company uses John’s blockchain address, the signature, and the data to be verified.
- Step-10:
If the signature is valid, the output will be true, or else an error message will occur. Once the signature verifies, John is permitted to enter the network.
Let’s move on to the next part in this how does blockchain work simply explained guide.
Blockchain Working in Various Sectors
Blockchain can work in various sectors such as healthcare, supply chain management, government, trade, financial institutions, real estate, insurance, and many more. The healthcare industry can highly benefit from this integration.
But you must be wondering how does blockchain work in healthcare anyway? Well, blockchain can work in healthcare very efficiently, offering a great deal of patient security. More so, it can deal with counterfeit drugs, patient privacy, and many more when the blockchain will work in healthcare.
On the other hand, supply chain management or trading will get seamless real-time tracking of products, quality checks, and source authentication process.
Governments or financial institutions need more than public (Ethereum) blockchains. They need a permissioned access (Hyperledger, EEA, and Corda) where the system would be decentralized but also ensure the privacy of sensitive information.
These are a few examples of how blockchain can work in different sectors.
Ending Note
Blockchain is here to stay, and most importantly, many enterprises are already pursuing the technology in their own way. According to Gartner, blockchain is going to be $3.1 trillion marketplaces by the year 2030.
But what do all these mean? It means that most of the companies will have their own blockchain solution, and the business model change drastically in the upcoming years. In reality, it will surely affect your business as well, and there’s no way you can just skip integrating the technology and still prevail in the market.
So, it’s high time you learned how blockchain works and how you can implement it into your system. Blockchain training courses can help in this regard. The great news is, our certified enterprise blockchain professional course offers everything you need to start your very first blockchain implementation.
Want to know more about Blockchain? Enroll now for Blockchain Certification and Courses!